第一篇wp
hh
一个虚拟机pwn,乍一看感觉有很多危险的点啊hhh
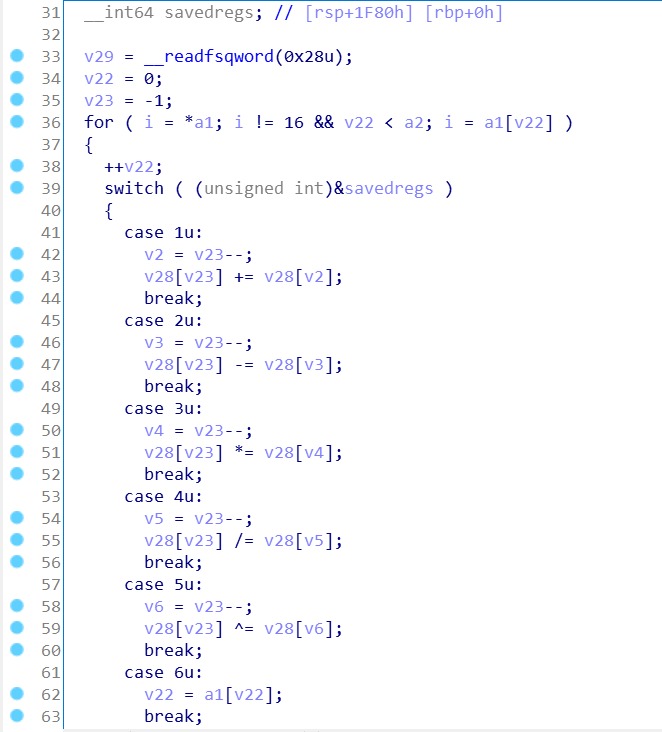
首先,输入是输入到bss段的,然后都是对栈上的数据做操作,而且下标是完全可以溢出的
例如,这里我用的是0xa:
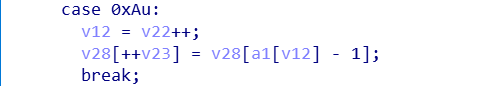
a1[v12]-1是可控的,也就是说可以溢出v28数组外,在栈上任意取数据写进v28
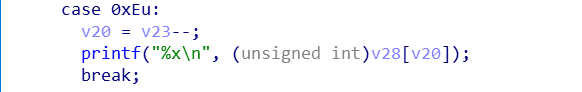
再配合上0xe的输出功能,就可以泄露栈上的libc地址了
由于程序开了沙箱,我们就需要在返回地址处写上orw链
分析程序,要写到返回地址,第一步,写数据到v28数组,第二步,越界迁移v28的数据到返回地址处
我用的分别是以下两个功能:

a1[v11]可控,也就实现写任意数据到v28
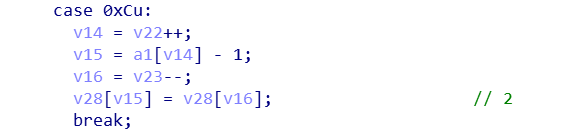
v15可控,即实现将v28的数据写到任意偏移处(返回地址)
完整exp:
(打比赛的时候懒得写函数了,看着乱hhh)
1 | from pwn import * |
ff
libc-2.32下的uaf:
不过,拥有很多的限制,edit只能两次,show只有一次
其次,edit,show和delete都只能对最近申请的chunk操作
之前没研究过libc-2.32,发现在chunk放入tcache的时候有些不一样,fd指针处并不像之前几个版本的tcache那样
不多说,直接翻源码
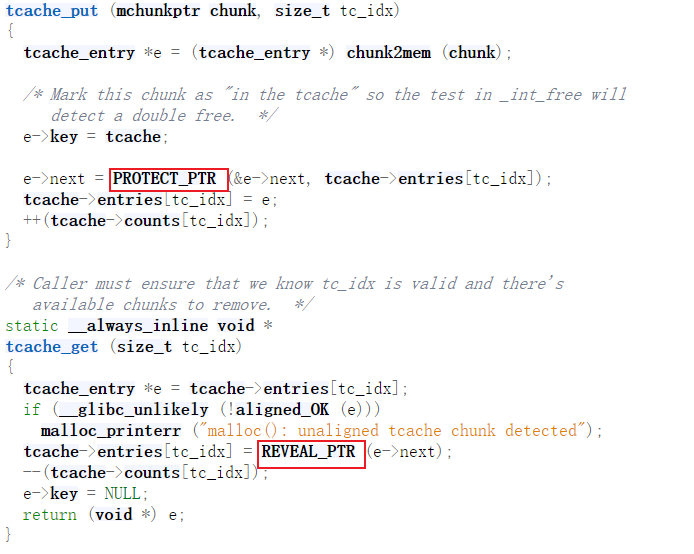
发现在tcache插入和取出时多了个PROTECT_PTR和REVEAL_PTR,看定义
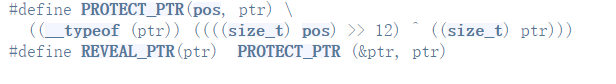
插入时将堆地址右移12位,与tcache->entries作抑或后写入fd
当tcache链上只有一个chunk时,fd的值即为chunk_addr>>12^0 = chunk_addr>>12
问题不大,还是可以借此泄露堆地址的
现在需要考虑的是,show只有一次,给堆地址还是libc?
我一开始是想给libc的,考虑之后发现,留给libc的话,泄露之后,没有edit,没有show,剩下就很难操作了
由于tcache插入的时候的PROTECT的,加上这题idx的局限性,使得链式攻击达到任意写比较难完成
泄露堆地址,攻击tcache结构体,布置entry成了一个办法,这样可以实现在堆内的多次任意写,然后申请到IO_FILE泄露libc
完整exp:
1 | from pwn import * |
white_give_flag
比赛时候不会,read返回0方法get